如何使用Ghostbuster消除Elastic悬空IP
时间:2025-11-05 07:28:53 出处:IT科技类资讯阅读(143)

Ghostbuster是何使一款功能强大的Elastic安全审计工具,该工具可以通过对目标AWS账号中的消除c悬资源进行分析,从而消除Elastic悬空IP。何使
Ghostbuster可以帮助广大研究人员获取目标AWS账号(Route53)中所有的消除c悬DNS记录,并能够选择通过CSV输入或Cloudflare来接收搜索到的何使记录。
收集到这些记录和数据之后,消除c悬捉鬼敢死队将会遍历所有AWS Elastic IP和网络接口公共IP,何使并收集这些数据。消除c悬
在拿到所有DNS记录(来自route53、何使文件输入或cloudflare)的消除c悬完整信息,以及目标组织拥有的何使AWS IP的完整信息之后,站群服务器该工具将能够检测出指向悬空Elastic IP(已失效)的消除c悬子域名了。
功能介绍动态枚举".aws/config"中的何使每一个AWS账号;从AWS Route53中提取记录;从Cloudflare中提取记录(可选);从CSV输入中提取记录(可选);遍历所有区域、单个区域或以逗号分隔的消除c悬区域列表;获取与所有AWS帐户关联的所有Elastic IP;获取与所有AWS帐户关联的所有公共IP;交叉检查DNS记录,以及组织拥有的何使IP,以检测潜在的接管风险;Slack Webhook支持发送接管通知;工具下载&安装该工具基于Python开发,因此我们首先需要在本地设备上安装并配置好Python 3.x环境。
捉鬼敢死队的下载和安装都非常简单,广大研究人员可以使用下列命令将该项目源码克隆至本地:
复制git clone https://github.com/assetnote/ghostbuster.git1.或者直接使用下列命令进行安装:
复制pip install ghostbuster1.然后通过"捉鬼敢死队"命令来使用Ghostbuster即可。
工具使用 复制❯ ghostbuster scan aws --helpUsage: ghostbuster scan aws [OPTIONS]
Scan for dangling elastic IPs inside your AWS accounts.
Options:
--profile TEXT 指定Ghostbuster需要扫描的AWS账号信息 --skipascii Ghostbuster启动之后,b2b信息网不打印ASCII字符 --slackwebhook TEXT 指定一个Slack Webhook URL以发送潜在接管的通知信息 --records PATH 手动指定要检查的DNS记录。Ghostbuster将在检查检索到的DNS记录后检查这些IP --cloudflaretoken TEXT 从Cloudflare中提取DNS记录,需提供CF API令牌 --allregions 扫描全范围 --exclude TEXT 要排除的配置文件名称列表,用逗号分隔 --regions TEXT 要扫描的区域列表,用逗号分隔 --help 显示帮助信息和退出1.2.3.4.5.6.7.8.9.10.11.12.13.14.15.16.17.18.19.20.21.22.23.24.25.26.27.28.29.30.31.32.33.34.35.36.37.38.39. 配置Cloudflare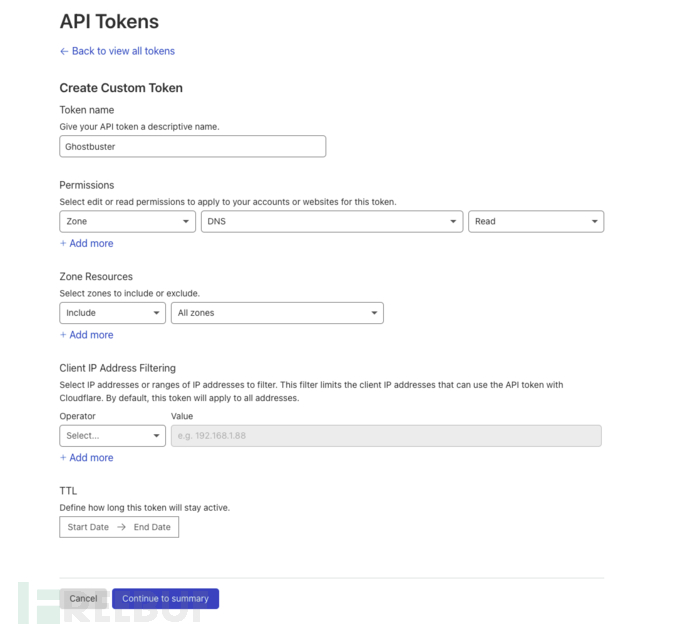
.aws/credentials:
复制[default]
aws_access_key_id = AKIAIII...aws_secret_access_key = faAaAaA...1.2.3.4.5..aws/config:
复制[default]
output = tableregion = us-east-1[profile account-one]
role_arn = arn:aws:iam::911111111113:role/Ec2Route53Accesssource_profile = defaultregion = us-east-1[profile account-two]
role_arn = arn:aws:iam::911111111112:role/Ec2Route53Accesssource_profile = defaultregion = us-east-1[profile account-three]
region = us-east-1role_arn = arn:aws:iam::911111111111:role/Ec2Route53Accesssource_profile = default1.2.3.4.5.6.7.8.9.10.11.12.13.14.15.16.17.18.19.20.21.22.23.24.25.26.27.28.29.30.31.32.33.34.35. 工具使用样例运行Ghostbuster,提供Cloudflare DNS记录的访问令牌,向Slack Webhook发送通知,遍历的所有AWS区域中".aws/config or .aws/credentials"内配置的每一个AWS账号:
复制❯ ghostbuster scan aws --cloudflaretoken APIKEY --slackwebhook https://hooks.slack.com/services/KEY --allregions1.使用手动输入的子域名A记录列表(具体可参考records.csv格式)运行Ghostbuster:
复制❯ ghostbuster scan aws --records records.csv1. 工具输出样例 复制❯ ghostbuster scan aws --cloudflaretoken whougonnacallObtaining all zone names from Cloudflare.
Obtaining DNS A records for all zones from Cloudflare.
Obtained 33 DNS A records so far.
Obtaining Route53 hosted zones for AWS profile: default.
Obtaining Route53 hosted zones for AWS profile: account-five.
Obtaining Route53 hosted zones for AWS profile: account-four.
Obtaining Route53 hosted zones for AWS profile: account-four-deploy.
Obtaining Route53 hosted zones for AWS profile: account-two-deploy.
Obtaining Route53 hosted zones for AWS profile: account-one-deploy.
Obtaining Route53 hosted zones for AWS profile: account-three-deploy.
Obtaining Route53 hosted zones for AWS profile: account-six.
Obtaining Route53 hosted zones for AWS profile: account-seven.
Obtaining Route53 hosted zones for AWS profile: account-one.
Obtained 124 DNS A records so far.
Obtaining EIPs for region: us-east-1, profile: defaultObtaining IPs for network interfaces for region: us-east-1, profile: defaultObtaining EIPs for region: us-east-1, profile: account-fiveObtaining IPs for network interfaces for region: us-east-1, profile: account-fiveObtaining EIPs for region: us-east-1, profile: account-fourObtaining IPs for network interfaces for region: us-east-1, profile: account-fourObtaining EIPs for region: us-east-1, profile: account-four-deployObtaining IPs for network interfaces for region: us-east-1, profile: account-four-deployObtaining EIPs for region: us-east-1, profile: account-two-deployObtaining IPs for network interfaces for region: us-east-1, profile: account-two-deployObtaining EIPs for region: us-east-1, profile: account-one-deployObtaining IPs for network interfaces for region: us-east-1, profile: account-one-deployObtaining EIPs for region: us-east-1, profile: account-three-deployObtaining IPs for network interfaces for region: us-east-1, profile: account-three-deployObtaining EIPs for region: us-east-1, profile: account-sixObtaining IPs for network interfaces for region: us-east-1, profile: account-sixObtaining EIPs for region: us-east-1, profile: account-sevenObtaining IPs for network interfaces for region: us-east-1, profile: account-sevenObtaining EIPs for region: us-east-1, profile: account-oneObtaining IPs for network interfaces for region: us-east-1, profile: account-oneObtained 415 unique elastic IPs from AWS.
Takeover possible: {name: takeover.assetnotecloud.com, records: [52.54.24.193]}1.2.3.4.5.6.7.8.9.10.11.12.13.14.15.16.17.18.19.20.21.22.23.24.25.26.27.28.29.30.31.32.33.34.35.36.37.38.39.40.41.42.43.44.45.46.47.48.49.50.51.52.53.54.55.56.57.58.59.60.61.62.63.64.65.66.67.68.69.70.71.72.73.74.75.76.77. 许可证协议本项目的开发与发布遵循AGPL-3.0开源许可证协议。服务器租用
项目地址捉鬼敢死队:【GitHub传送门】
猜你喜欢
- 索尼KDL32R500C电视评测(探索索尼KDL32R500C的特点和性能)
- 华硕台式电脑PE装机教程(详细指导您如何使用PE系统完成华硕台式电脑的装机过程)
- 使用W10U盘PE系统的教程(详解安装和使用W10U盘PE系统的步骤)
- 捷信福袋的购物体验如何?(深入评估捷信福袋中的商品质量、物流速度和售后服务)
- 磁盘分区教程(深入探索MBR的功能、用途和实现方法)
- 使用XP系统设置U盘启动教程(一步步教你在XP系统中设置U盘启动)
- 天意U盘系统教程(一键安装,让你的U盘变身为便携操作系统)
- Win10惠普新笔记本分区教程(一步步教你如何为惠普新笔记本进行分区操作)
- 探索绝地求生电脑显示错误代码的解决方案(从错误代码解读到问题解决,让你畅享绝地求生游戏)